Unix is an incredibly well-designed operating system. After all, it cannot be a coincidence that not only Linux distros but Mac OS X also runs on it. Unix comes with excellent security features, customizable file permissions are one of them. Unix file permissions allow you to define who can read, write, and execute each file on your system.
If you have a WordPress site or use a Linux server with another type of site you will find this tutorial useful. Web hosts usually allow users to change Unix file permissions from their cPanel so that they can achieve extra security by protecting vulnerable files and directories at the root level.
File Ownership
The most important thing you need to know is that Unix treats everything as a file. Not only files but directories and devices are also files on a Unix system. Unix assigns three types of owners to each file: User, Group, and Other. To configure your file permissions, you need to decide which rights you want to grant to each of those owners.
1. User
The User is the person who created the given file. Anyone who creates a new file in a Unix system will automatically be granted User rights over that file.
2. Group
Group usually contains more than one users. Everyone who belongs to the same user group as User will be automatically the member of Group. You can use Group if you want to assign group permissions to a certain file. For instance, you can allow (or forbid) to the whole group to read, write, or execute a file with just one command.
3. Other
Finally, Other means everyone else who can access the file. Unix treats them as the third kind of owners, and you can set separate permissions for them. Essentially, members of the Other group are users who neither created the file nor belong to the same user group as the person who created the file.
File Permissions
Every file on a Unix system comes with three kinds of permissions: Read, Write, and Execute. You can set each kind separately. With the help of these permissions, you can grant or deny reading, writing, and executing rights to the three aforementioned owner types (User, Group, Other).
1. Read (r)
The Read permission grants users the right to open or read a file. The user can only see the contents of the file but cannot modify it. When the Read permission belongs to a directory, the user can only list its contents but cannot modify or delete it.
2. Write (w)
Write allows users to edit the contents of a file. When the Write permission is set on a directory, users can add, rename, and remove all the files residing in the directory.
3. Execute (x)
The Execute permission means that a user can run the file as a program. Execute makes sense when you work with an executable file, for instance a script. Unlike Windows, Unix doesn’t allow anyone to run a file as a program unless the Execute permission is set for them.
Bringing Owners & Permissions Together
Unix has a great way to let you know which permissions are set for each file in a directory. You only need to open your terminal and navigate into the folder you are interested in. You can do that by using the cd Unix command. For instance, if you want to navigate into the directory called etc you need to enter the following command:
cd etcWhen you are inside the directory, you can list its contents by entering this command:
ls -laAs you can see on the screenshot below, this command shows all the files inside the directory, together with their Unix file permissions:
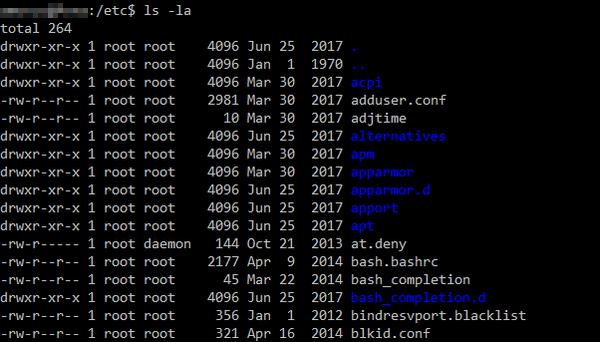
Inside my terminal, directories are blue and files are white (your terminal may use different colors, however). You can see the file permissions in the first column. For instance, drwxr-xr-x is a file permission. Unix file permissions are composed according to the following rules:
- 1st character – directory (d) or file (-)
- 2-3-4th characters – User‘s permissions: read (r), write (w), execute (x)
- 5-6-7th characters – Group‘s permissions: read (r), write (w), execute (x)
- 8-9-10th characters – Other‘s permissions: read (r), write (w), execute (x)
When an owner group doesn’t have a certain file permission granted, Unix uses a – sign. For instance, the drwxr-xr-x file permission means that the file:
- (d) is a directory (directories are also files in Unix).
- (rwx) User can read, write, and execute the file.
- (r-x) Group can read and execute the file but cannot read it.
- (r-x) Other can read and execute the file but cannot read it.
Using the same technique, you can decode the file permissions of any Unix file.
Numeric Mode
Unix also has a numeric mode to express file permissions. It’s important to know them because this is what you will see in your cPanel’s file manager. Besides, if you want to change the permissions from your Terminal you can also make use of the numeric mode. In numeric mode, each permission gets a number assigned to it, according to the following rules:
- 4 = r (read)
- 2 = w (write)
- 1 = x (execute)
Let’s have a look at some frequently used file permissions to see how it works in practice (in numeric mode, it’s not indicated whether the file is a single file or a directory):
- 444 = Owner can read (4), Group can read (4), Other can read (4) the file.
- 644 = Owner can read and write (4+2=6), Group can read (4), Other can read (4) the file.
- 604 = Owner can read and write (4+2=6), Group can do nothing (0), Other can read (4) the file.
- 777 = Owner can read, write, execute (4+2+1=7), Group can read, write, execute (4+2+1=7), Other can read, write, execute (4+2+1=7). This is the least restrictive permission; it’s considered dangerous by most sysadmins.
Using this technique, you can calculate the numeric equivalent of every possible file permission combination. However, there are some combinations that are rarely (or never) used as they make little sense (e.g. 333).
Most control management systems (CMS) come with typical file permissions they use on the websites they power. For instance, WordPress uses 755 and 644 across its file system. In the WP Codex, you can read more about WordPress’ file permissions.
Changing Unix File Permissions from cPanel
If you open the File Manager inside your cPanel you can see and change the Unix file permissions on your server. Below, you can see the file system of a (somewhat customized) WordPress install, with the file permissions in the right column:
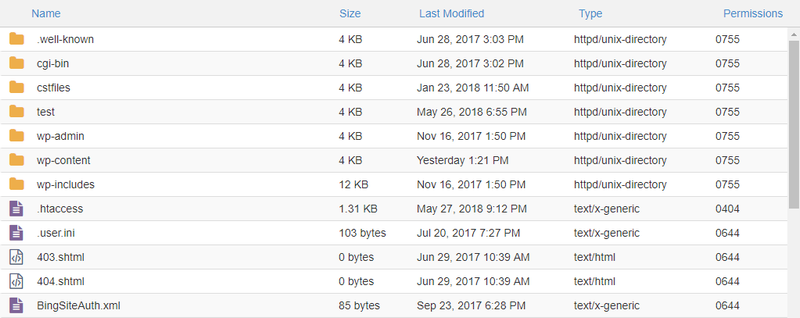
As I mentioned, WordPress uses 755 and 644 for its core files. On the screenshot above, the file permission for the .htaccess file has been manually changed to 404 as it’s more secure than the original 644. However, a strict permission like that may cause problems on some servers—you need to experiment to see what works for your specific server configuration (if 404 throws an error you can also try 444).
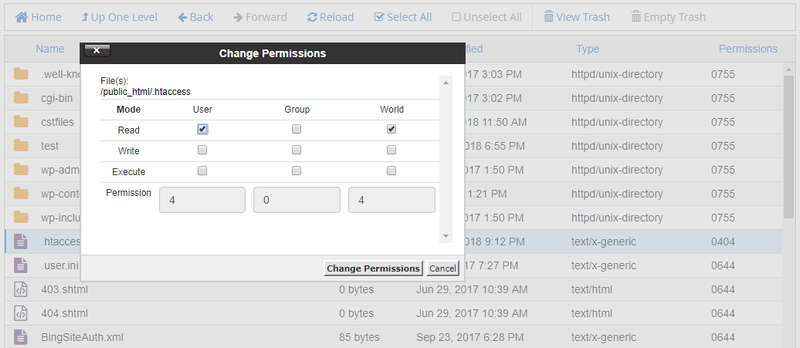
If you want to change the file permissions of a file or directory you only need to right-click the file inside the File Manager, click the Change Permissions menu, and choose the permissions you want:
Using the chmod Command
You can also change file permissions from your terminal, using the chmod command. Navigate into the directory in which the file resides with the aforementioned cd command. Then, type the following command into your terminal (it changes the file permission to 644):
chmod 644 [yourfile]If you are not the owner of the file you may also need to add the sudo command:
sudo chmod 644 [yourfile]It’s also possible to change the permission of every file and folder inside a directory. You only need to add the -R modifier (recursive permission change) to the previous command:
sudo chmod 644 -R [yourdirectory]Recursive permission change only works on directories.
Wrapping Up
As you can see, Unix is a smart system. If you know the rules you can quickly perform different tasks at the root level, such as improving security. Before you change your file permissions, always think about how it can affect your whole system.
If you want to learn more about how you can make your website more secure also take a look at our articles on PHP security measures and the best security plugins for WordPress. To stay updated with the latest web development tips, tricks, and news, don’t hesitate to follow Developer Drive on Facebook and Twitter, either.